buu寒假练习1
ycb_2020_easy_heap
程序在使用edit功能时出现了'\x00'字节溢出,很容易想到修改下一个chunk的prev_size 、size 和 PREV_INUSE标志位,让其与上边的unsorted chunk合并造成堆块重叠
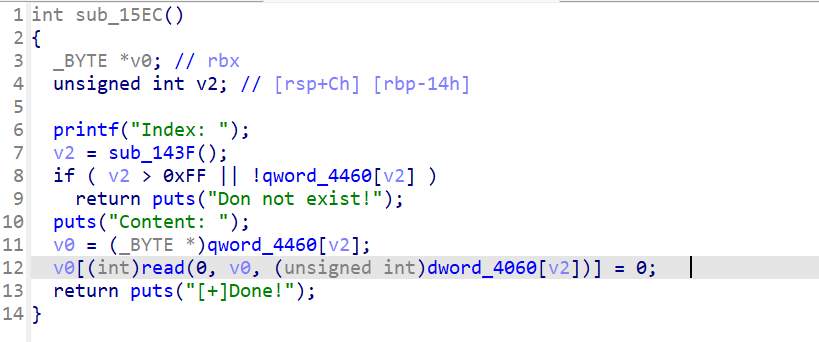
然而这里是libc-2.30.so,会对合并的上一个chunk的size检查,与修改的prev_size对比,这样以前的方法就不能继续使用了
1 | |
这种高版本的off-by-one总结如下:
- 让合并的chunk的size与伪造的prev_size相等,才能通过检查,但修改正常chunk的size是不可能的,所以在chunk中去伪造另一个chunk即可;
- 由于堆块的合并还要通过unlink的检查,main_arena和bss中一般并不存在我们伪造chunk的地址(当然有PIE保护也就不用考虑bss),所以需要先去泄漏堆地址,我们自己在堆上写入伪造chunk的地址;
- 与以前unlink攻击的思路一样,伪造chunk的fd和bk也是需要与我们写入的地址相对应的。
具体构造如下:
程序开了沙盒,在__free_hook中写入rdi与rdx转化的gedget,再与setcontext函数相结合劫持rsp到堆上,最后直接ROP或者使用mprotect后写入shellcode
完整的exp
1 | |
VNCTF2021 hh
vmpwn类型的题,指令和操作数都是4个字节,主要使用如下指令:
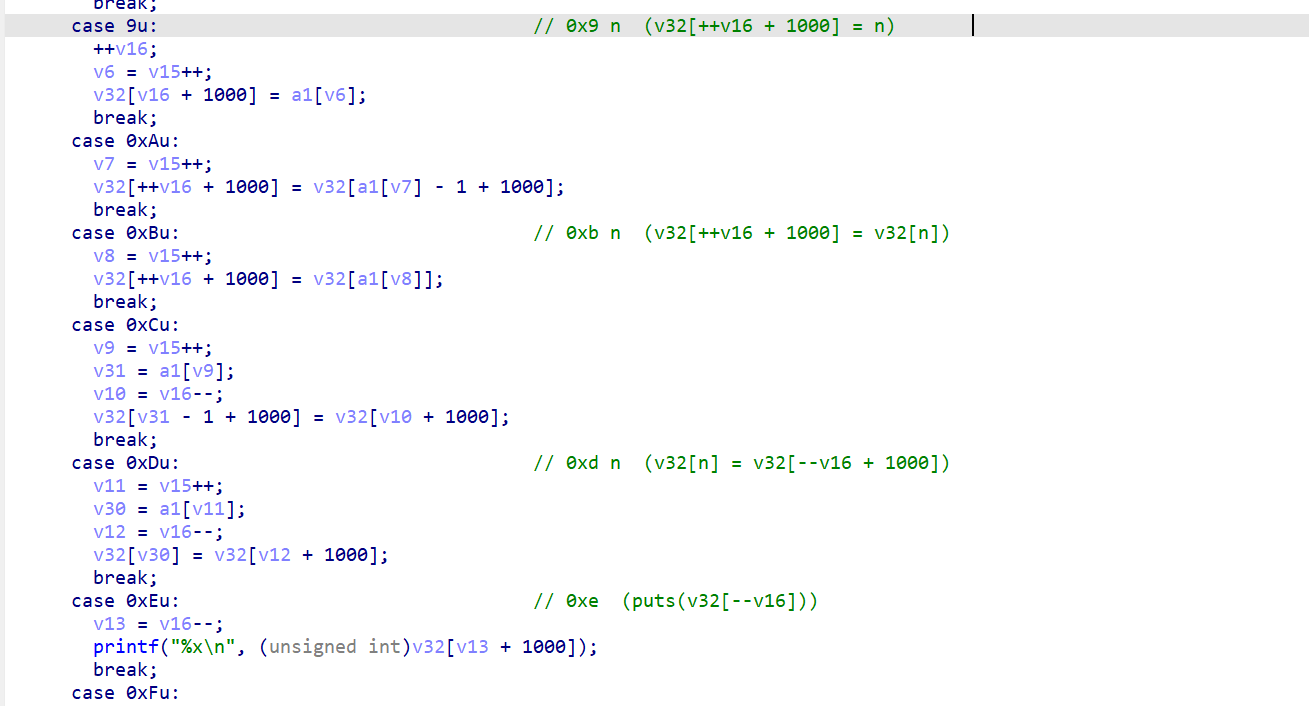
利用思路:
- v32存在于栈上,执行指令
0xb n时会造成数组越界,可以将栈上其它的内容写入v32数组,再配合指令0xe就可以泄漏栈地址和__libc_start_main地址; - 指令
0x9 n可以在v32数组上写入任何数,再配合指令0xd n,同样是数组越界将v32数组的内容写入到栈上其它地方,当然这里直接写入函数返回地址,执行ROP。
完整exp如下
1 | |
roarctf_2019_realloc_magic
Roderick师傅的这篇已经写得很好了,还需要注意的是使用realloc函数,在扩大内存时,并且tcache中正好有该大小的chunk,这时也并不会去使用tcache中的chunk。
自己复现的exp
1 | |